Support is a Windows machine categorized as Easy difficulty, featuring an SMB share that allows anonymous authentication. Upon connecting to the share, an executable file is uncovered, designed to query the machine’s LDAP server for available users. Through methods such as reverse engineering, network analysis, or emulation, the password utilized by the binary to bind the LDAP server is discerned, enabling further LDAP queries. Within the user list, a user named ‘support’ is identified, and his password is found in the ‘info’ field, facilitating a WinRM connection to the machine. Subsequently, domain information is gathered using tools like ‘SharpHound’, while ‘BloodHound’ exposes that the ‘Shared Support Accounts’ group, of which the ‘support’ user is a member, holds ‘GenericAll’ privileges on the Domain Controller. Leveraging a Resource-Based Constrained Delegation attack results in obtaining a shell as ‘NT Authority\System’.
Given that the Kerberos and LDAP services are operational, it’s likely that we’re dealing with a Windows Active Directory environment.
On the “Support” machine by 0xdf on Hack The Box, the challenge revolves around exploiting a domain controller with certain vulnerabilities. Here’s a breakdown of the steps involved:
- Anonymous Authentication on SMB Server: The machine features a domain controller with SMB services allowing anonymous authentication. This vulnerability enables access to certain resources without requiring valid credentials.
- Program Hosting the Password for User “ldap”: Within the SMB server, there’s a program containing the password for the user “ldap”. Gaining access to this password provides a foothold for further exploitation.
- Dumping Active Directory Objects: Using the credentials obtained from the “ldap” user, accessible Active Directory objects are dumped. During this process, an LDAP attribute for the user “support” is discovered, containing their password.
- Abusing Support’s Access: The “support” user possesses full access over the domain controller’s machine account. This access is exploited to change the password for the machine account and subsequently dump the NTDS secrets.
- Obtaining Administrator Hash: From the NTDS secrets, the administrator’s hash is extracted. This hash is a crucial step towards gaining elevated privileges.
- Using WinRM to Gain Administrator Access: Leveraging the administrator’s hash obtained from NTDS secrets, WinRM is employed to establish a shell as the Administrator. This action grants full control over the system.
By following these steps, the machine “Support” can be fully compromised, demonstrating various aspects of privilege escalation and exploitation in a Windows Active Directory environment.
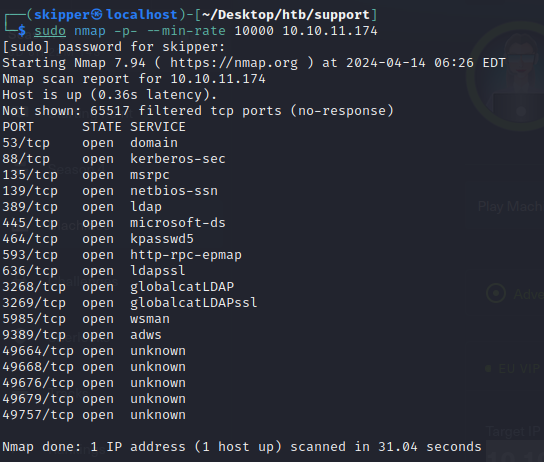
Some services mentioned in the scan results are 53/DNS, 88/Kerberos, and 389/LDAP. The presence of these ports together indicates that this machine is likely an Active Directory domain controller.
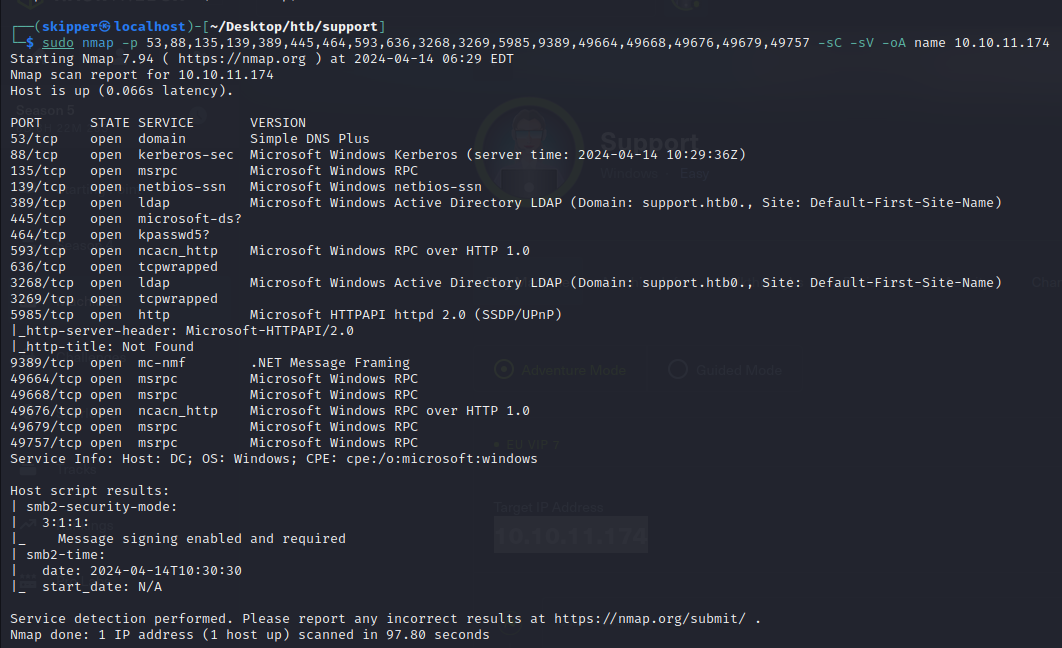
When tackling a Windows server with numerous ports, I typically adopt a strategic approach by prioritizing based on familiarity. I create a tiered list, outlining potential avenues for exploration:
Must Look At:
- SMB: Scan for accessible shares to uncover potential valuable information.
- LDAP: Explore for any accessible data without requiring credentials.
If the above yield no results:
- Kerberos: Attempt username brute-forcing. Any discovered usernames could be susceptible to AS-REP-Roasting attacks.
- DNS: Probe for zone transfer capabilities or attempt subdomain brute-forcing.
- RPC: Investigate if anonymous access is feasible.
Note for credential-based approaches:
- WinRM: Search for credentials associated with users in the Remote Management Users group. Accessing such credentials could facilitate obtaining a shell.
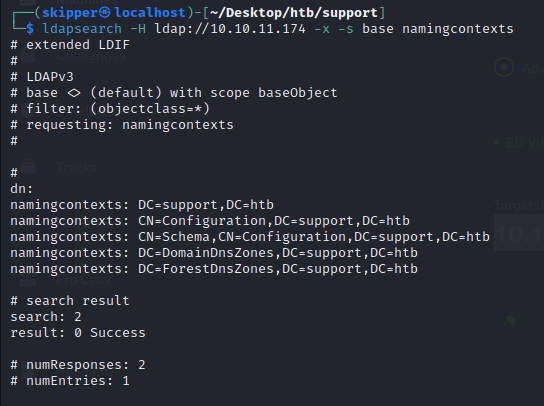
“ldapsearch -H ldap://10.10.11.174 -x -s base namingcontexts”, is used to query LDAP (Lightweight Directory Access Protocol) servers. Specifically, it requests the naming contexts from the LDAP server hosted at the IP address 10.10.11.174.
Here’s a breakdown of the command options:
- “-H ldap://10.10.11.174”: Specifies the LDAP server’s URI.
- “-x”: Uses simple authentication instead of SASL (Simple Authentication and Security Layer).
- “-s base”: Specifies the search scope as base, meaning it searches only the base object.
- “namingcontexts”: The attribute to search for, which typically retrieves the naming contexts configured on the LDAP server.
This command could help identify the base distinguished name (DN) or naming contexts configured on the LDAP server, which is often essential for further LDAP queries and understanding the directory structure.



